| Citation: |
Lianjun Jiang, Dongdong Li, Yuqiang Fang, Meisheng Zhao, Ming Liu, Zhilin Xie, Yukang Zhao, Yanlin Tang, Wei Jiang, Houlin Fang, Rui Ma, Lei Cheng, Weifeng Yang, Songtao Han, Shibiao Tang. Countermeasure against blinding attack for single-photon detectors in quantum key distribution[J]. Journal of Semiconductors, 2024, 45(4): 042702. doi: 10.1088/1674-4926/45/4/042702
L J Jiang, D D Li, Y Q Fang, M S Zhao, M Liu, Z L Xie, Y K Zhao, Y L Tang, W Jiang, H L Fang, R Ma, L Cheng, W F Yang, S T Han, S B Tang. Countermeasure against blinding attack for single-photon detectors in quantum key distribution[J]. J. Semicond, 2024, 45(4): 042702. doi: 10.1088/1674-4926/45/4/042702
Export: BibTex EndNote
|
Countermeasure against blinding attack for single-photon detectors in quantum key distribution
doi: 10.1088/1674-4926/45/4/042702
More Information-
Abstract
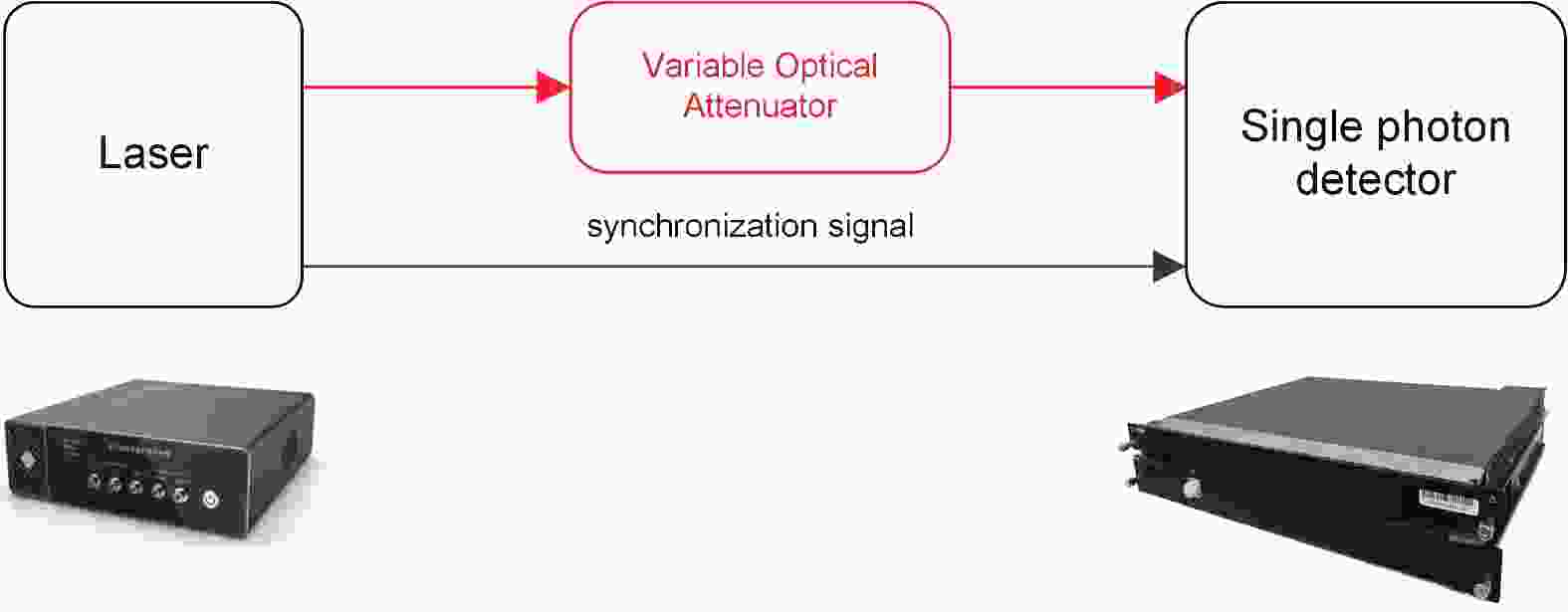
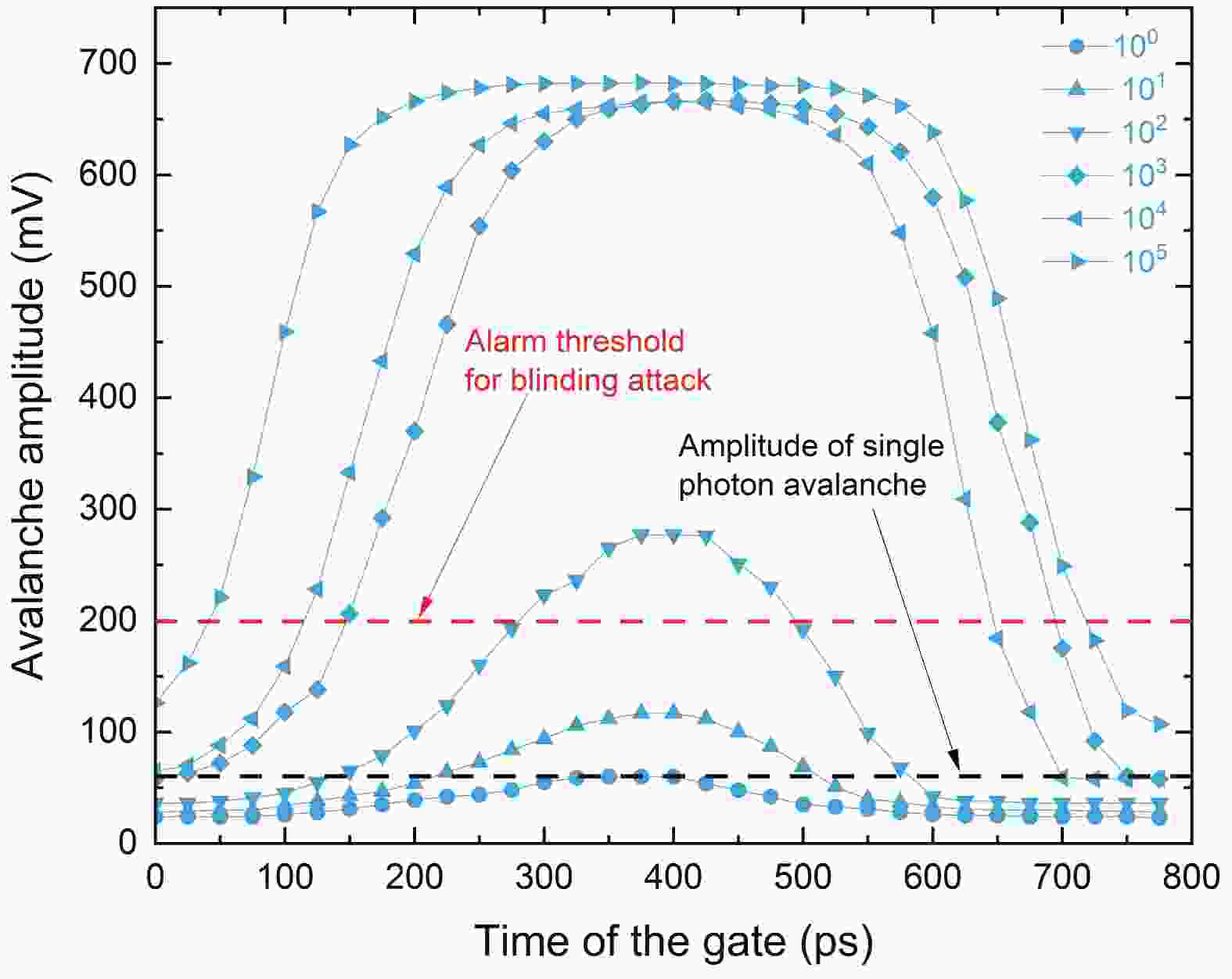
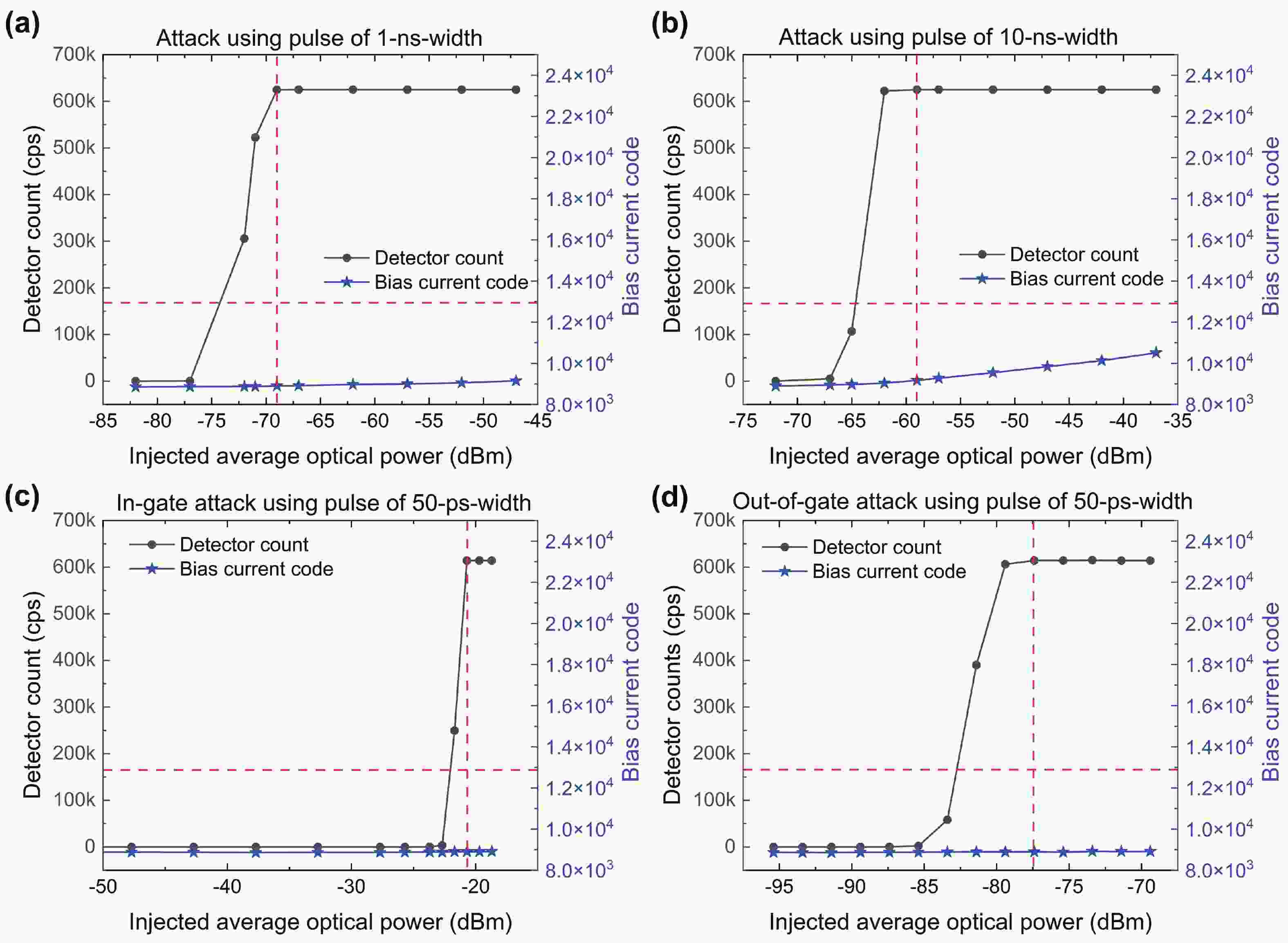
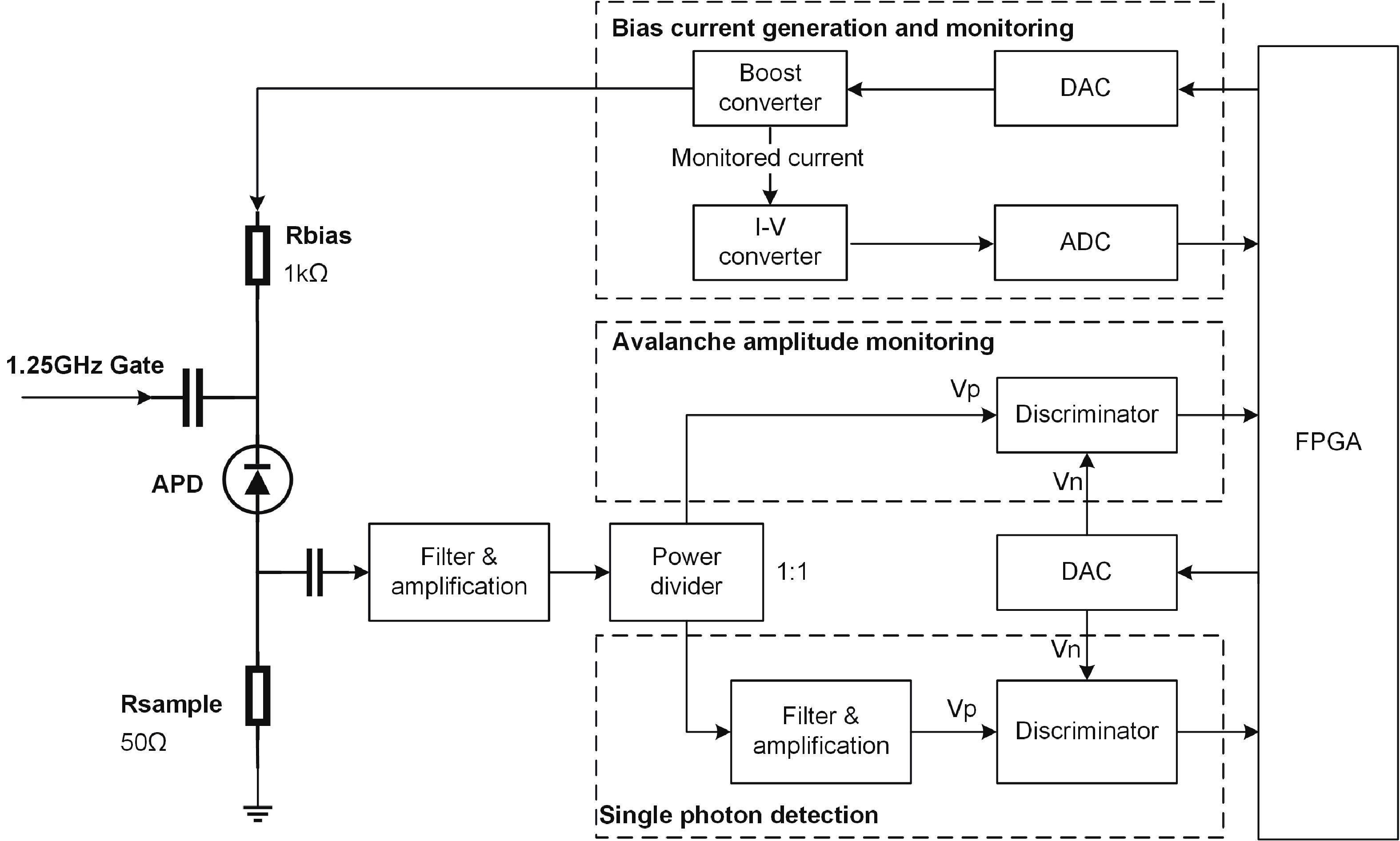
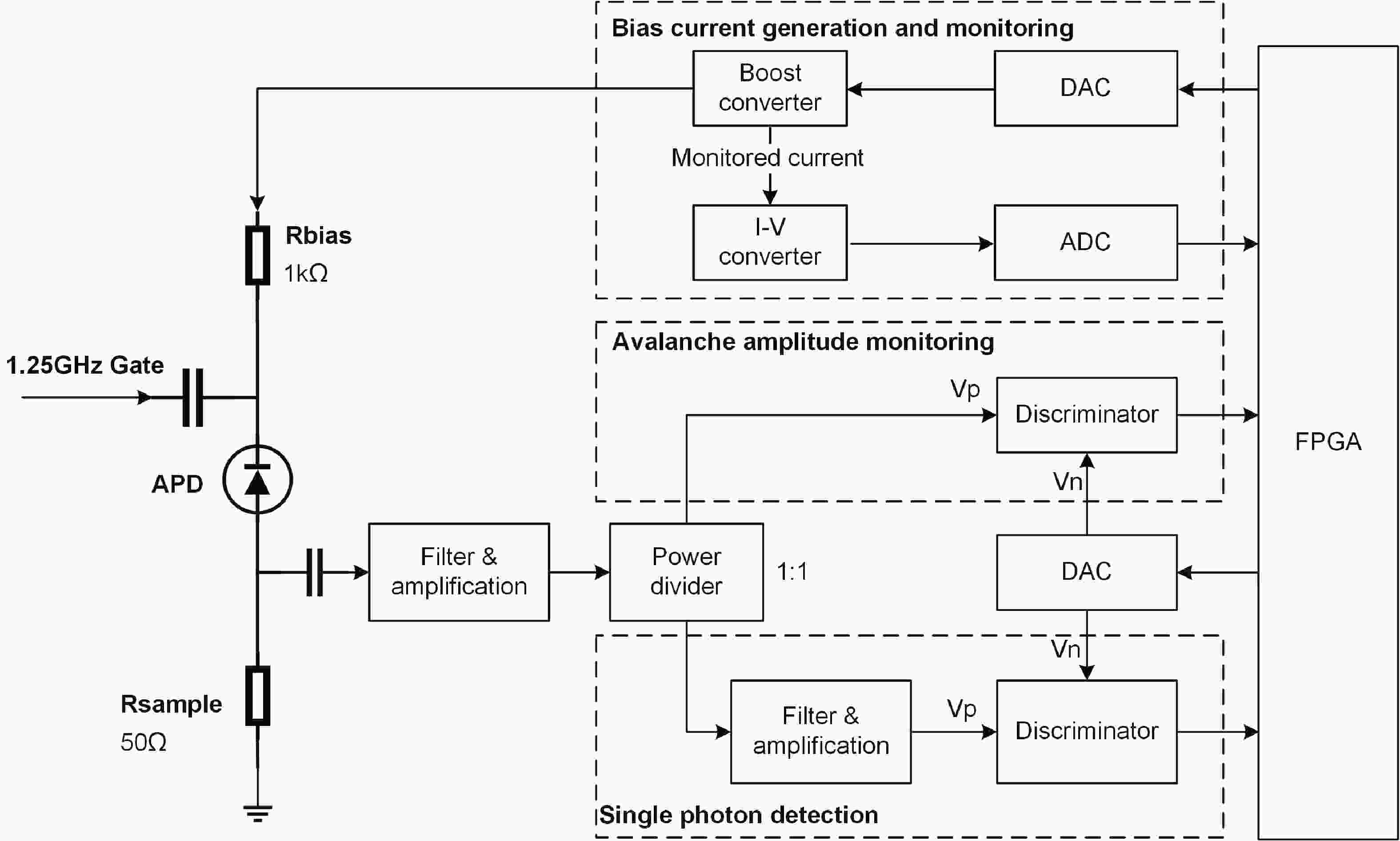
Quantum key distribution (QKD), rooted in quantum mechanics, offers information-theoretic security. However, practical systems open security threats due to imperfections, notably bright-light blinding attacks targeting single-photon detectors. Here, we propose a concise, robust defense strategy for protecting single-photon detectors in QKD systems against blinding attacks. Our strategy uses a dual approach: detecting the bias current of the avalanche photodiode (APD) to defend against continuous-wave blinding attacks, and monitoring the avalanche amplitude to protect against pulsed blinding attacks. By integrating these two branches, the proposed solution effectively identifies and mitigates a wide range of bright light injection attempts, significantly enhancing the resilience of QKD systems against various bright-light blinding attacks. This method fortifies the safeguards of quantum communications and offers a crucial contribution to the field of quantum information security. -
References
[1] Gisin N, Ribordy G, Tittel W, et al. Quantum cryptography. Rev Mod Phys, 2002, 74, 145 doi: 10.1103/RevModPhys.74.145[2] Scarani V, Bechmann-Pasquinucci H, Cerf N J, et al. The security of practical quantum key distribution. Rev Mod Phys, 2009, 81, 1301 doi: 10.1103/RevModPhys.81.1301[3] Wu Y L, Bao W S, Cao S R, et al. Strong quantum computational advantage using a superconducting quantum processor. Phys Rev Lett, 2021, 127, 180501 doi: 10.1103/PhysRevLett.127.180501[4] Zhong H S, Wang H, Deng Y H, et al. Quantum computational advantage using photons. Science, 2020, 370, 1460 doi: 10.1126/science.abe8770[5] Zhang Q, Xu F H, Chen Y A, et al. Large scale quantum key distribution: Challenges and solutions. Opt Express, 2018, 26, 24260 doi: 10.1364/OE.26.024260[6] Pirandola S, Andersen U L, Banchi L, et al. Advances in quantum cryptography. Adv Opt Photonics, 2020, 12, 1012 doi: 10.1364/AOP.361502[7] Liu Q, Huang Y M, Du Y Q, et al. Advances in chip-based quantum key distribution. Entropy, 2022, 24, 1334 doi: 10.3390/e24101334[8] Peng C Z, Zhang J, Yang D, et al. Experimental long-distance decoy-state quantum key distribution based on polarization encoding. Phys Rev Lett, 2007, 98, 010505 doi: 10.1103/PhysRevLett.98.010505[9] Li D D, Zhao M S, Li Z, et al. High dimensional quantum key distribution with temporal and polarization hybrid encoding. Opt Fiber Technol, 2022, 68, 102828 doi: 10.1016/j.yofte.2022.102828[10] Tang Y L, Zhou C, Li D D, et al. Time-Bin phase-encoding quantum key distribution using Sagnac-based optics and compatible electronics. Opt Express, 2023, 31, 26335 doi: 10.1364/OE.496723[11] Boaron A, Boso G, Rusca D, et al. Secure quantum key distribution over 421 km of optical fiber. Phys Rev Lett, 2018, 121, 190502 doi: 10.1103/PhysRevLett.121.190502[12] Liu Y, Zhang W J, Jiang C, et al. Experimental twin-field quantum key distribution over 1000 km fiber distance. Phys Rev Lett, 2023, 130, 210801 doi: 10.1103/PhysRevLett.130.210801[13] Li W, Zhang L K, Tan H, et al. High-rate quantum key distribution exceeding 110 Mb s–1. Nat Photonics, 2023, 17, 416 doi: 10.1038/s41566-023-01166-4[14] Chen T Y, Wang J, Liang H, et al. Metropolitan all-pass and inter-city quantum communication network. Opt Express, 2010, 18, 27217 doi: 10.1364/OE.18.027217[15] Li D D, Gao S, Li G C, et al. Field implementation of long-distance quantum key distribution over aerial fiber with fast polarization feedback. Opt Express, 2018, 26, 22793 doi: 10.1364/OE.26.022793[16] Tang Y L, Xie Z L, Zhou C, et al. Field test of quantum key distribution over aerial fiber based on simple and stable modulation. Opt Express, 2023, 31, 26301 doi: 10.1364/OE.494318[17] Zhou F, Yong H L, Li D D, et al. Study on quantum key distribution between different media. Acta Phys Sin, 2014, 63, 140303 doi: 10.7498/aps.63.140303[18] Li D D, Shen Q, Chen W, et al. Proof-of-principle demonstration of quantum key distribution with seawater channel: Towards space-to-underwater quantum communication. Opt Commun, 2019, 452, 220 doi: 10.1016/j.optcom.2019.07.037[19] Chen T Y, Jiang X, Tang S B, et al. Implementation of a 46-node quantum metropolitan area network. NPJ Quantum Inf, 2021, 7, 134 doi: 10.1038/s41534-021-00474-3[20] Dynes J F, Wonfor A, Tam W W S, et al. Cambridge quantum network. NPJ Quantum Inf, 2019, 5, 101 doi: 10.1038/s41534-019-0221-4[21] Ribezzo D, Zahidy M, Vagniluca I, et al. Deploying an inter-european quantum network. Adv Quantum Technol, 2023, 6, 2200061 doi: 10.1002/qute.202200061[22] Liao S K, Yong H L, Liu C, et al. Long-distance free-space quantum key distribution in daylight towards inter-satellite communication. Nat Photonics, 2017, 11, 509 doi: 10.1038/nphoton.2017.116[23] Liao S K, Cai W Q, Liu W Y, et al. Satellite-to-ground quantum key distribution. Nature, 2017, 549, 43 doi: 10.1038/nature23655[24] Chen Y A, Zhang Q, Chen T Y, et al. An integrated space-to-ground quantum communication network over 4, 600 kilometres. Nature, 2021, 589, 214 doi: 10.1038/s41586-020-03093-8[25] Lu C Y, Cao Y, Peng C Z, et al. Micius quantum experiments in space. Rev Mod Phys, 2022, 94, 035001 doi: 10.1103/RevModPhys.94.035001[26] Gottesman D, Lo H K, Lütkenhaus N, et al. Security of quantum key distribution with imperfect devices. Quantum Inf Comput, 2004, 4, 325 doi: 10.1109/ISIT.2004.1365172[27] Xu F H, Ma X F, Zhang Q, et al. Secure quantum key distribution with realistic devices. Rev Mod Phys, 2020, 92, 025002 doi: 10.1103/RevModPhys.92.025002[28] Li D D, Tang Y L, Zhao Y K, et al. Security of optical beam splitter in quantum key distribution. Photonics, 2022, 9, 527 doi: 10.3390/photonics9080527[29] Wang Y, Du G H, Xu Y B, et al. Practical security of high-dimensional quantum key distribution with intensity modulator extinction. Entropy, 2022, 24, 460 doi: 10.3390/e24040460[30] Sun S H, Huang A Q. A review of security evaluation of practical quantum key distribution system. Entropy, 2022, 24, 260 doi: 10.3390/e24020260[31] Makarov V. Controlling passively quenched single photon detectors by bright light. New J Phys, 2009, 11, 065003 doi: 10.1088/1367-2630/11/6/065003[32] Lydersen L, Wiechers C, Wittmann C, et al. Hacking commercial quantum cryptography systems by tailored bright illumination. Nat Photonics, 2010, 4, 686 doi: 10.1038/nphoton.2010.214[33] Gerhardt I, Liu Q, Lamas-Linares A, et al. Full-field implementation of a perfect eavesdropper on a quantum cryptography system. Nat Commun, 2011, 2, 349 doi: 10.1038/ncomms1348[34] Wiechers C, Lydersen L, Wittmann C, et al. After-gate attack on a quantum cryptosystem. New J Phys, 2011, 13, 013043 doi: 10.1088/1367-2630/13/1/013043[35] Weier H, Krauss H, Rau M, et al. Quantum eavesdropping without interception: An attack exploiting the dead time of single-photon detectors. New J Phys, 2011, 13, 073024 doi: 10.1088/1367-2630/13/7/073024[36] Zhao Y, Fung C H F, Qi B, et al. Quantum hacking: Experimental demonstration of time-shift attack against practical quantum-key-distribution systems. Phys Rev A, 2008, 78, 042333 doi: 10.1103/PhysRevA.78.042333[37] Qian Y J, He D Y, Wang S, et al. Hacking the quantum key distribution system by exploiting the avalanche-transition region of single-photon detectors. Phys Rev Appl, 2018, 10, 064062 doi: 10.1103/PhysRevApplied.10.064062[38] Jain N, Wittmann C, Lydersen L, et al. Device calibration impacts security of quantum key distribution. Phys Rev Lett, 2011, 107, 110501 doi: 10.1103/PhysRevLett.107.110501[39] Beaudry N J, Moroder T, Lütkenhaus N. Squashing models for optical measurements in quantum communication. Phys Rev Lett, 2008, 101, 093601 doi: 10.1103/PhysRevLett.101.093601[40] Pinheiro P V P, Chaiwongkhot P, Sajeed S, et al. Eavesdropping and countermeasures for backflash side channel in quantum cryptography. Opt Express, 2018, 26, 21020 doi: 10.1364/OE.26.021020[41] Yuan Z L, Dynes J F, Shields A J. Avoiding the blinding attack in QKD. Nat Photonics, 2010, 4, 800 doi: 10.1038/nphoton.2010.269[42] Yuan Z L, Dynes J F, Shields A J. Resilience of gated avalanche photodiodes against bright illumination attacks in quantum cryptography. Appl Phys Lett, 2011, 98, 231104 doi: 10.1063/1.3597221[43] Gras G, Sultana N, Huang A, et al. Optical control of single-photon negative feedback avalanche diode detector. J Appl Phys, 2020, 127, 094502 doi: 10.1063/1.5140824[44] Wu Z H, Huang A Q, Chen H, et al. Hacking single-photon avalanche detectors in quantum key distribution via pulse illumination. Opt Express, 2020, 28, 25574 doi: 10.1364/OE.397962[45] Gao B W, Wu Z H, Shi W X, et al. Ability of strong-pulse illumination to hack self-differencing avalanche photodiode detectors in a high-speed quantum-key-distribution system. Phys Rev A, 2022, 106, 033713 doi: 10.1103/PhysRevA.106.033713[46] Zhang J, Eraerds P, Walenta N, et al. 2.23 GHz gating InGaAs/InP single-photon avalanche diode for quantum key distribution. SPIE Defense, Security, and Sensing. Proc SPIE 7681, Advanced Photon Counting Techniques IV, Orlando, Florida, USA. 2010, 7681, 239 doi: 10.1117/12.862118[47] Fang Y Q, Chen W, Ao T H, et al. InGaAs/InP single-photon detectors with 60% detection efficiency at 1550 nm. Rev Sci Instrum, 2020, 91, 083102 doi: 10.1063/5.0014123 -
Proportional views
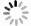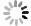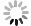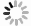




 DownLoad:
DownLoad: