| Citation: |
Xiangyu Li, Pengyuan Jiao, Chaoqun Yang. Side-channel attack-resistant AES S-box with hidden subfield inversion and glitch-free masking[J]. Journal of Semiconductors, 2021, 42(3): 032402. doi: 10.1088/1674-4926/42/3/032402
****
X Y Li, P Y Jiao, C Q Yang, Side-channel attack-resistant AES S-box with hidden subfield inversion and glitch-free masking[J]. J. Semicond., 2021, 42(3): 032402. doi: 10.1088/1674-4926/42/3/032402.
|
Side-channel attack-resistant AES S-box with hidden subfield inversion and glitch-free masking
DOI: 10.1088/1674-4926/42/3/032402
More Information
-
Abstract
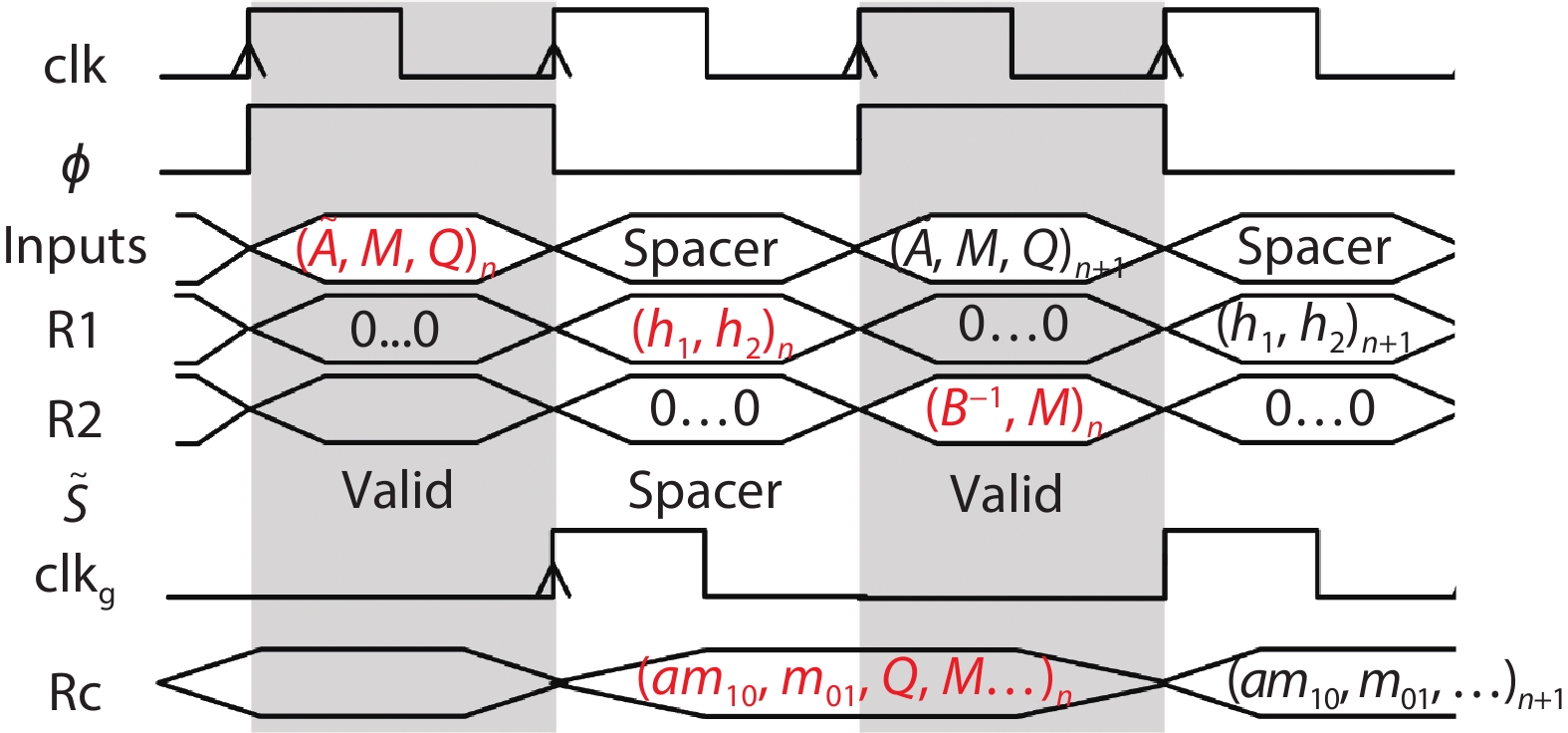
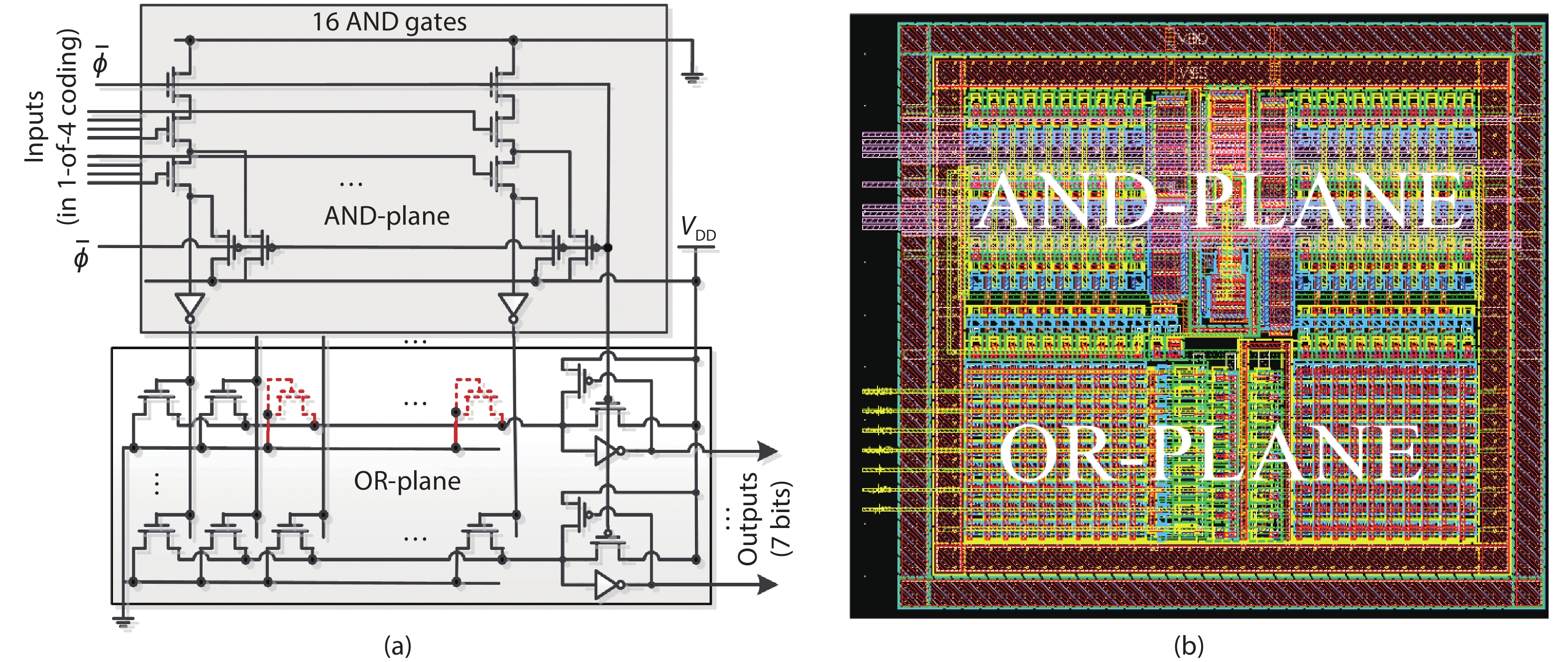
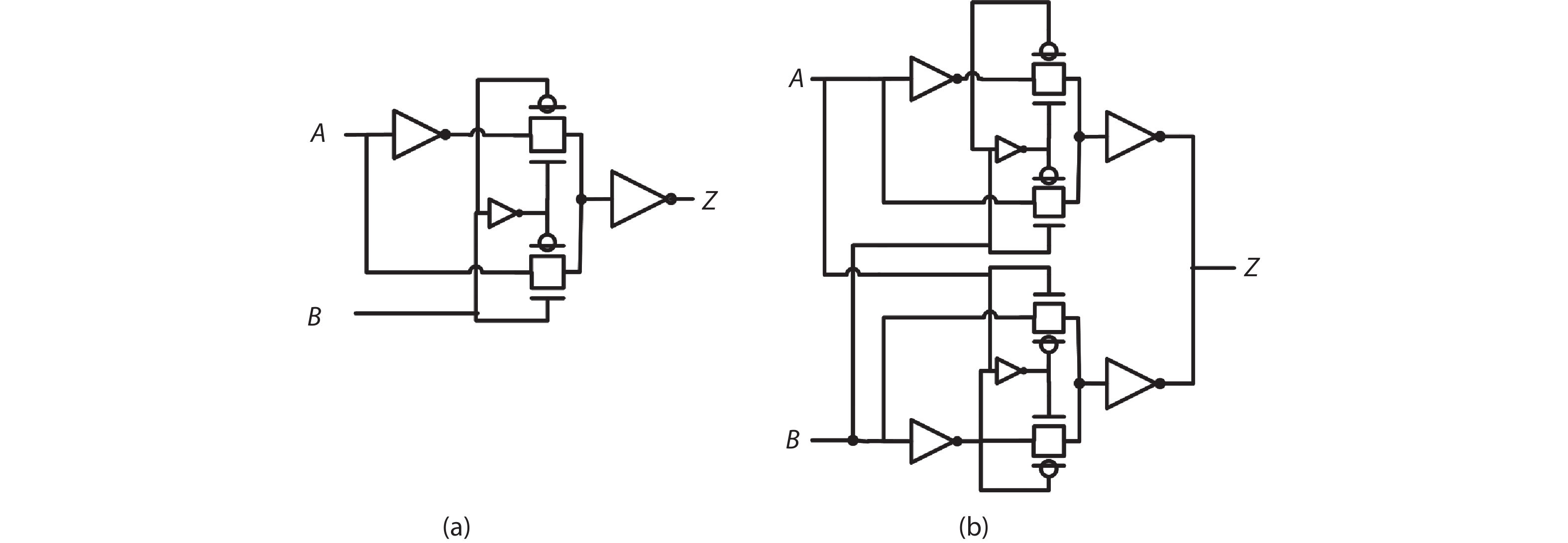
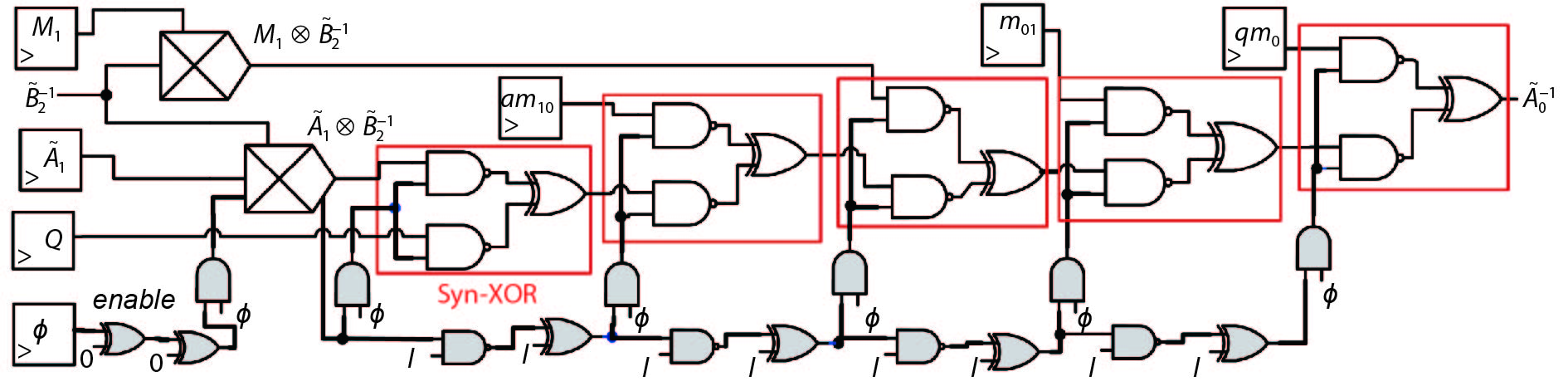
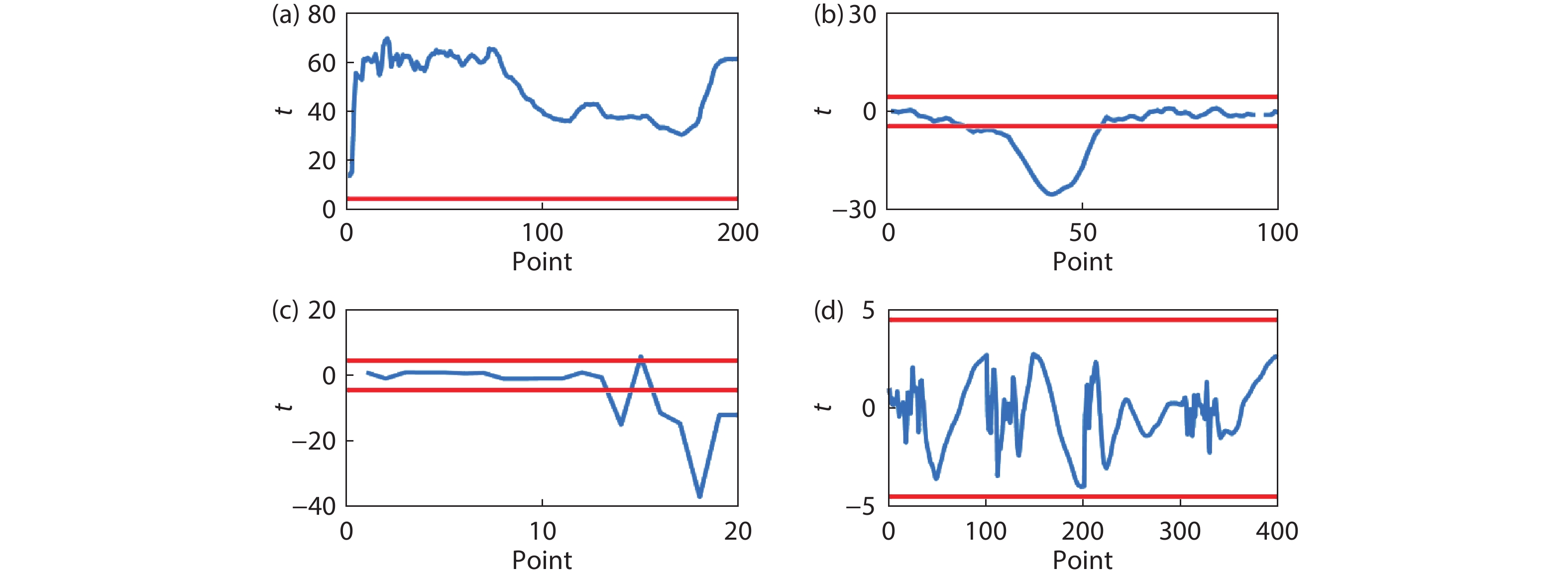
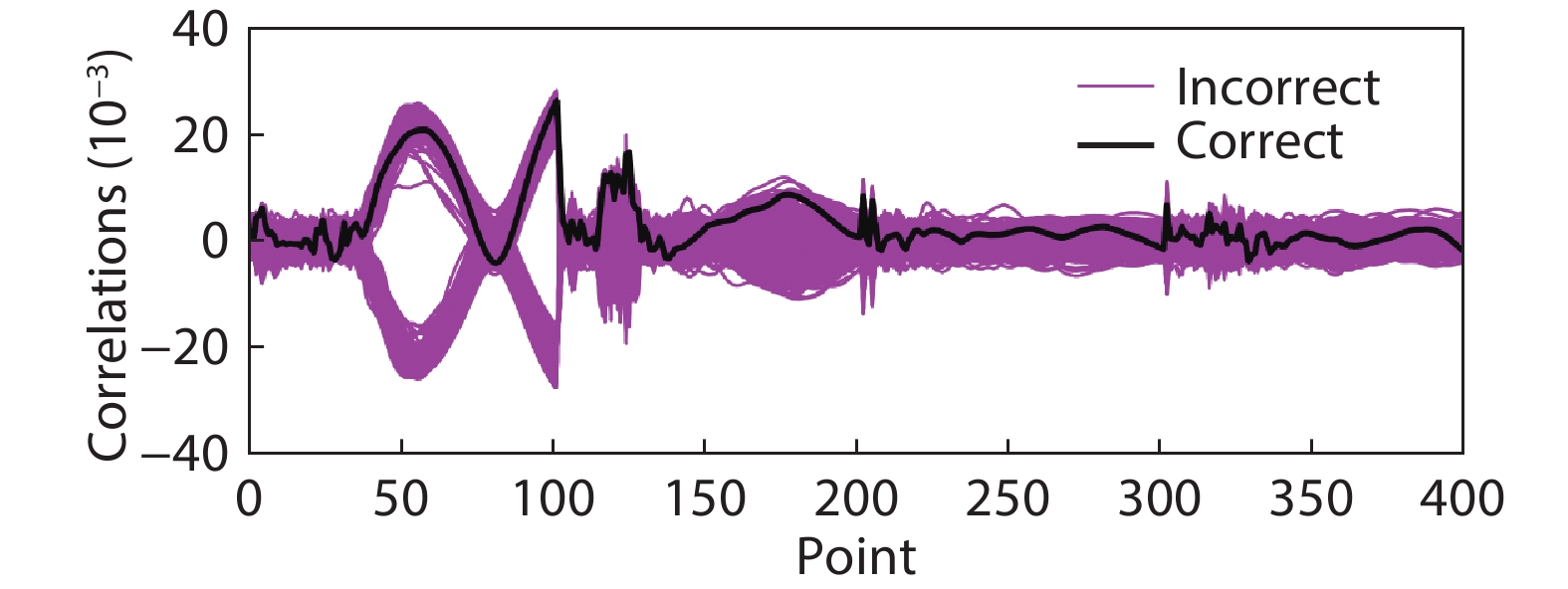
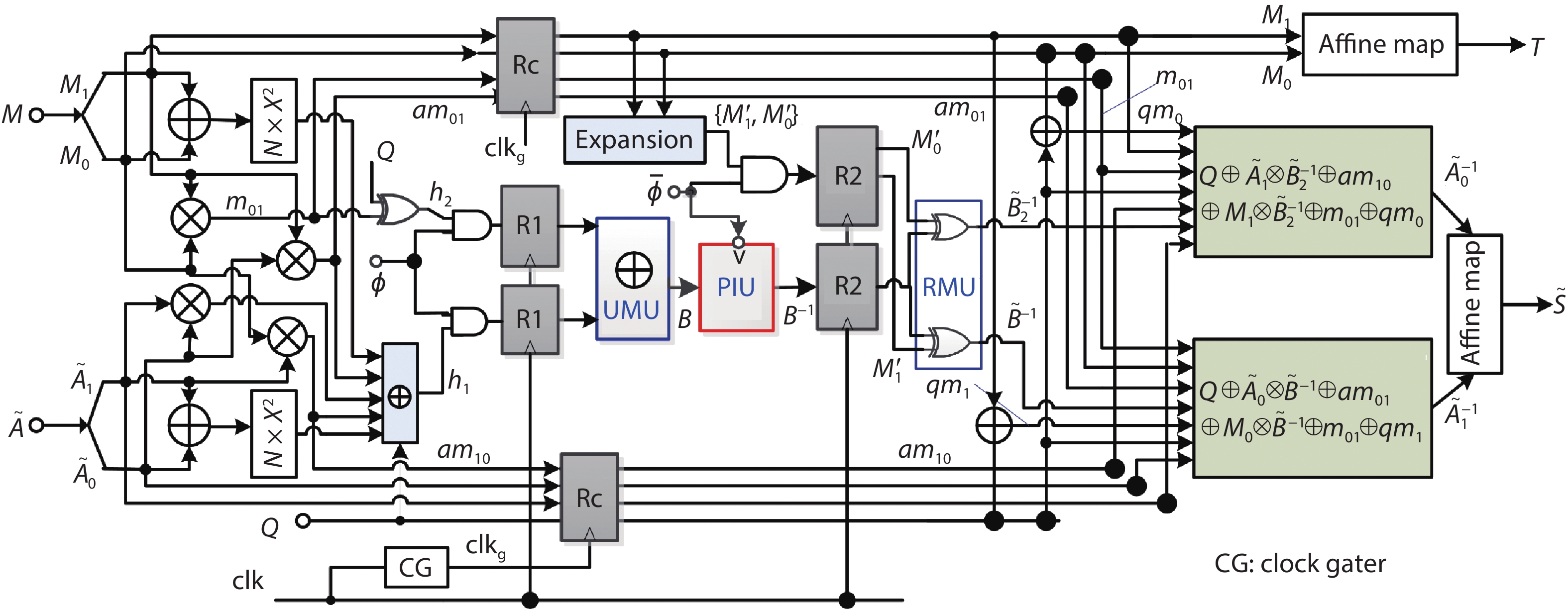
A side-channel attack (SCA)-resistant AES S-box implementation is proposed, which is an improvement from the power-aware hiding (PAH) S-box but with higher security and a smaller area. We use the composite field approach and apply the PAH method to the inversion in the nonlinear kernel and a masking method to the other parts. In addition, a delay-matched enable control technique is used to suppress glitches in the masked parts. The evaluation results show that its area is contracted to 63.3% of the full PAH S-box, and its power-delay product is much lower than that of the masking implementation. The leakage assessment using simulation power traces concludes that it has no detectable leakage under t-test and that it at least can thwart the moment-correlation analysis using 665 000 noiseless traces.-
Keywords:
- ASIC,
- side-channel attack,
- AES S-box,
- power-aware hiding,
- glitch-free
-
References
[1] Dinu D, Kizhvatov I. EM analysis in the IoT context: Lessons learned from an attack on thread. IACR Trans Cryptogr Hardw Embed Syst, 2018, 73[2] Tsai K L, Huang Y L, Leu F Y, et al. AES-128 based secure low power communication for LoRaWAN IoT environments. IEEE Access, 2018, 6, 45325 doi: 10.1109/ACCESS.2018.2852563[3] Taha M, Schaumont P. Key updating for leakage resiliency with application to AES modes of operation. IEEE Trans Inform Forensic Secur, 2015, 10, 519 doi: 10.1109/TIFS.2014.2383359[4] Moradi A, Poschmann A, Ling S, et al. Pushing the limits: A very compact and a threshold implementation of AES. Adv Cryptol - EUROCRYPT 2011, 2011, 69 doi: 10.1007/978-3-642-20465-4_6[5] Gao S, Roy A, Oswald E. Constructing TI-friendly substitution boxes using shift-invariant permutations. Cryptographers Track RSA Conference, 2019, 433[6] Boss E, Grosso V, Güneysu T, et al. Strong 8-bit Sboxes with efficient masking in hardware extended version. J Cryptogr Eng, 2017, 7, 149 doi: 10.1007/s13389-017-0156-7[7] Burns F, Bystrov A, Koelmans A, et al. Security evaluation of balanced 1-of-n circuits. IEEE Trans VLSI Syst, 2011, 19, 2135 doi: 10.1109/TVLSI.2010.2064793[8] Liu P C, Chang H C, Lee C Y. A low overhead DPA countermeasure circuit based on ring oscillators. IEEE Trans Circuits Syst II, 2010, 57, 546 doi: 10.1109/TCSII.2010.2048400[9] Singh A, Kar M, Mathew S, et al. Improved power side channel attack resistance of a 128-bit AES engine with random fast voltage dithering. European Solid-State Device Research Conference, 2017, 51[10] van Woudenberg J G J, Witteman M F, Bakker B. Improving differential power analysis by elastic alignment. Cryptographers Track RSA Conference, 2011, 104[11] Lu S, Zhang Z, Papaefthymiou M C. A 1.25 pJ/bit 0.048 mm2 AES core with DPA resistance for IoT devices. IEEE Asian Solid-State Circuits Conference, 2017, 65[12] Ma J S, Wang M Y, Li X Y. Power-aware hiding method for S-box protection. Electron Lett, 2014, 50, 1604 doi: 10.1049/el.2014.1559[13] Li X Y, Yang C Q, Ma J S, et al. Energy-efficient side-channel attack countermeasure with awareness and hybrid configuration based on it. IEEE Trans VLSI Syst, 2017, 25, 3355 doi: 10.1109/TVLSI.2017.2752212[14] Yang C Q, Li X Y, Yin S J. Low-cost energy-efficient side-channel attacks resistant AES S-box with power-aware hiding inverter in GF(24). International Conference on Trust, Security and Privacy in Computing and Communications, 2018, 1526[15] Canright D, Batina L. A very compact “perfectly masked” S-box for AES. Applied Cryptography and Network Security. Berlin, Heidelberg: Springer Berlin Heidelberg, 2008, 446[16] Nikova S, Rijmen V, Schläffer M. Secure hardware implementation of nonlinear functions in the presence of glitches. J Cryptol, 2011, 24, 292 doi: 10.1007/s00145-010-9085-7[17] Canright D. A very compact S-box for AES. Conference on Cryptographic Hardware and Embedded Systems, 2005, 441[18] Schneider T, Moradi A. Leakage assessment methodology. Conference on Cryptographic Hardware and Embedded Systems, 2015, 495[19] Moradi A, Standaert F X. Moments-correlating DPA. Proceedings of the 2016 ACM Workshop on Theory of Implementation Security - TIS'16, 2016, 5[20] Zeng J L, Wang Y, Xu C, et al. Improvement on masked S-box hardware implementation. IEEE International Conference on Innovations in Information Technology, 2012, 113 -
Proportional views




 DownLoad:
DownLoad: